
Text message authentication revealed as worst kind of MFA for cyber security

Multifactor authentication (MFA) is "not enough" defence against cyberattacks as Business Email Compromise (BEC) incidents remained the most reported in 2024, according to a new research.
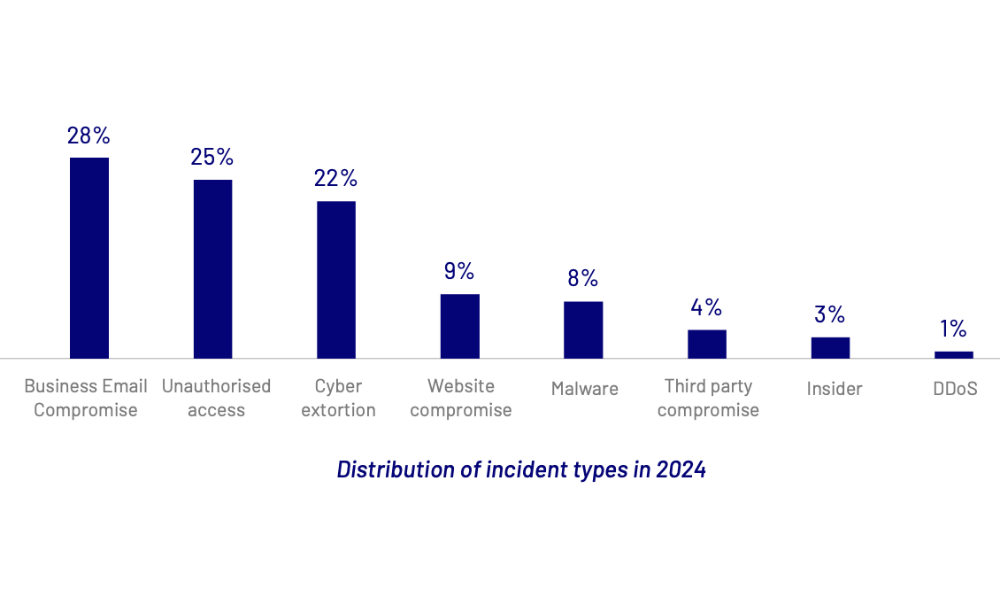
Findings from CyberCX revealed that 28% of cybersecurity incidents reported in 2024 are a BEC type, where criminals compromise a victim's email accounts, typically through phishing emails.
Implementing MFA has been used by various organisations to defend against phishing attacks by requiring users to provide multiple forms of identification aside from passwords.
But CyberCX's findings revealed that MFA is not slowing BEC, as 75% of incidents involve a method of bypassing MFA called session hijacking.
"For the last three years, phishing kits with session hijacking capabilities have continuously grown in use," the report read. "The increase is likely due to the continued proliferation of MFA in all organisations and the followed response of the threat actors."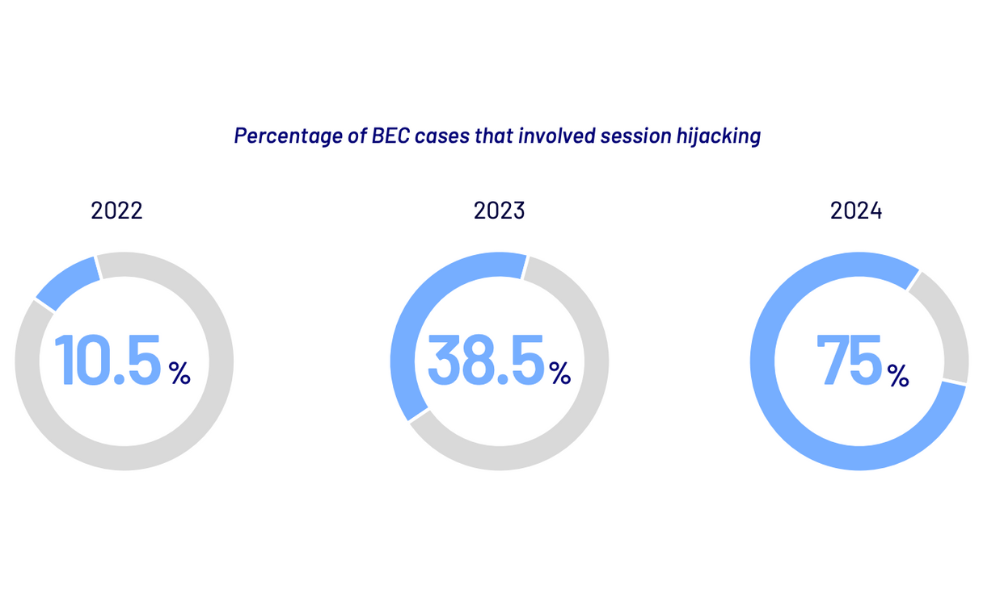
Hamish Krebs, Executive Director of Digital Forensics and Incident Response at CyberCX, said text message authentication is the worst of the MFA options, Radio New Zealand reported.
According to Krebs, utilising push notifications on a phone is the most common tactic for threat actors, who will push the authentication prompt until the user agrees to it.
"That happens all the time. You don't really want to have a situation where your phone is bothering you to allow a multi-factor authentication," Krebs told RNZ.
"Imagine that phone beeps you five, six, seven, eight, nine times and you're in a meeting - eventually you just say, 'accept.' It goes away, but that lets the bad guys in."
Krebs noted that some of the highest-profile security incidents involved an administrator who clicked an illegitimate MFA prompt because it bothered them on their phone.
Overall, Krebs noted that the global cyber threat landscape has continued to deteriorate as threat actors evolve their tactics and increase the tempo of their attacks.
"Malicious actors are moving into your cloud infrastructure more than ever before, cyber extortion groups continue to iterate their foul business despite well-publicised disruption by global law enforcement, and the widespread deployment of tools like Endpoint Detection and Response (EDR) is driving changes to the way adversaries compromise networks," Krebs said in a statement.
To be prepared for the threat of cyberattacks, CyberCX suggested taking the following steps: