
IT teams 'powerless to prevent sensitive data leaks and block access from compromised devices, increasing the risk of data losses'

Employees under hybrid and remote work have been cited as the top source of security risk by chief information security officers (CISO), according to a new report.
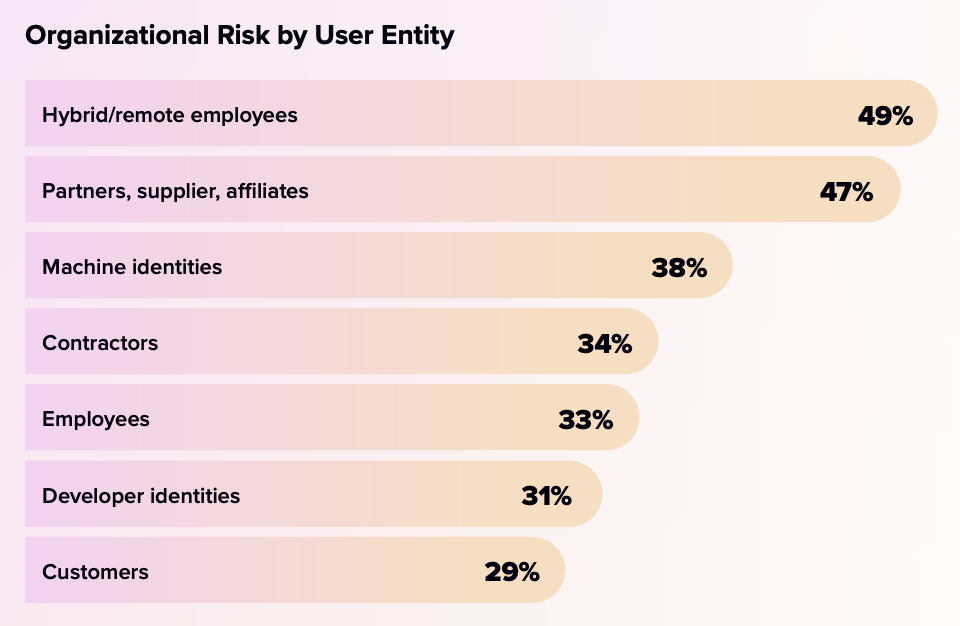
The report, released by 1Password, revealed that 49% of CISOs cite remote and hybrid workers as a top source of security risk to their organisations.
Others have cited partners, suppliers, and affiliates (47%), as well as machine identities (38%), according to the report.
Source: 1Password
The report attributed the risk to the rise of remote and hybrid employees, which has grown from 70% to 80% since 2020.
"The profound tectonic shifts in how companies have worked over the last two years have grown the Access-Trust Gap from a small fissure into a vast chasm," said Jason Meller, VP of Product at 1Password, in a statement.
The Access-Trust Gap has been defined by 1Password as the difference between the users, applications, and devices that a business trusts to access sensitive data, and those that can access it in practice.
According to the report, while access is critical to improve workplace productivity, it can also lead to "overly permissive sign-ins" from unregistered and untrusted devices.
"This leaves security and IT teams powerless to prevent sensitive data leaks and block access from compromised devices, increasing the risk of data losses," the report read.
Jay Bretzmann, Research Vice President at IDC, said this vulnerability stems from traditional security tools not keeping up with the modern workplace.
"As organisations embrace hybrid work, addressing the Access-Trust Gap is more urgent than ever," Bretzmann said in a statement. "With the growing complexities of remote work and the rise of AI-driven threats, organisations need solutions that can meet modern security demands while still enabling productivity."
To close the Access-Trust Gap, the IDC suggested the following measures:
"A future-looking access management solution should extend the strengths of identity access management and mobile device management to unmanaged apps and devices, ensuring all access attempts are trusted and secure," Bretzmann said.